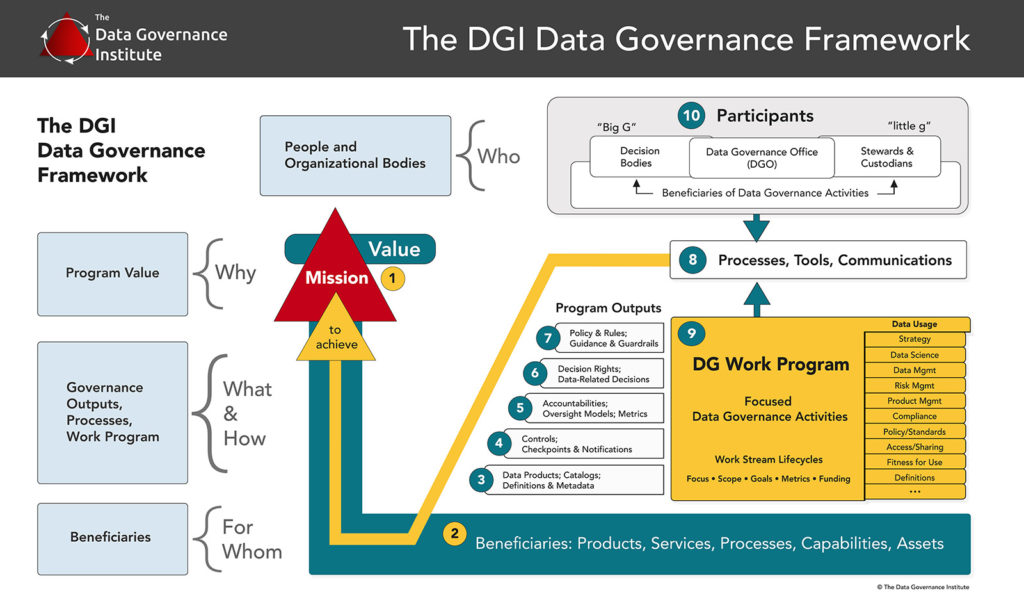
Framework Component #4: Controls
Data is constantly at risk.
With the proliferation of data breaches – and the consequences for those who were entrusted with the data – it is becoming clear that data can also represent risk. How do we deal with risk? We manage it, preferably by preventing the events that we don’t want to occur. Those we can’t be sure of preventing, we at least detect, so we can then correct the problem.

How are risk management strategies made operational? Through controls. Controls can be preventative or detective/corrective. They can be process controls or technical controls, automated, manual, or technology-enabled manual processes.
Often the Data Governance program is asked to recommend data-related controls that could be used to support governance goals. Data Governance may also be asked to recommend ways that existing general controls (Change Management, policies, training, life cycles, and Project Management, etc.) could be modified to support governance goals or enterprise goals.
Sometimes Data Governance is asked to assist with internal or external audits by explaining how different data-related controls build upon each other.
Data provides value.
Controls do more than manage risk. They also deliver value by increasing the likelihood that data, data products, and the processes that use them meet expectations. The controls may be executed by humans, or they may be embedded into automated routines or systems. They may focus on standardization, compliance with a requirement, or enabling data usage.
Data controls generally combine value and risk management.
Many data controls are designed to provide value, minimize costs, and manage risk simultaneously. An example are access governance controls, which enforce rules about WHO can view/update WHAT data about WHAT subjects, under WHAT circumstances.
Before an individual control is developed and implemented, designers make choices based on policy, guidance, and rules handed down from Data Access Governance teams. By understanding the business and compliance intent behind the guidance and rules, these designers can make informed decisions about how to develop and configure products that
- present the most value to authorized users of data points
- avoid duplication of effort between technical teams that serve both authorized users and unauthorized users
- employ existing authorization technology to switch the data on and off, depending upon the product user’s profile.